File Director
This page refers to an older version of the product.View the current version of the online Help.
Advanced configuration
Select Configuration > Advanced to access the Advanced options.
In this section:
- DSCP QoS configuration
- HTTP access
- TLS
- NTP
- Load Balancer status
- SMB storage authentication
- SMTP configuration
- Syslog server
- SSH Access
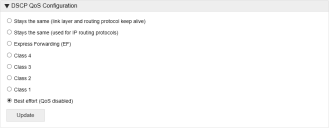
DSCP QoS configuration
This setting is only required if your organization uses Differentiated Services Code Point (DSCP) settings to help manage its network traffic.
The setting must be applied to in accordance with your organization’s networking requirements. Your network team will be able to advise which setting to apply.
In the DSCP QoS Configuration area of the Advanced options, select the required configuration and click Update.
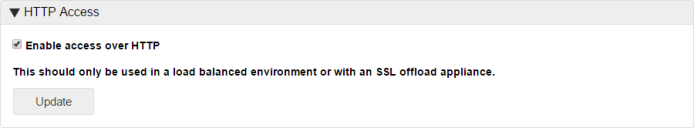
HTTP access
In the HTTP Access area of the Advanced options, configure the required setting and click Update to apply.
This option should only be used to enable connection by HTTP in a load balanced environment or with an SSL offload appliance.
Secure Session Cookies
For load balanced configurations where SSL offload is being used secure session cookies will not be issued automatically. If secure session cookies are required the load balancer request headers should be configured to include: x-secure-cookie=1
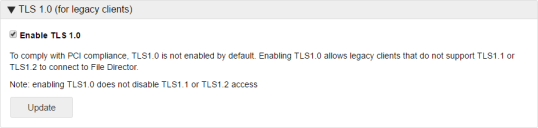
TLS 1.0
PCI compliance requires SSL v3/TLS 1.0 to be disabled in File Director. Configuring endpoints to default to a secure protocol (TLS 1.1 or TLS 1.2) requires the implementation of registry settings and potentially an update. Customers that are unable to implement this change can toggle TLS 1.0 on in File Director (version 4.2+).
For more information, see this Microsoft support article 3140245.
Select Configuration > Advanced and apply the Enable TLS 1.0 option as required.
When enabled, this is done across the whole cluster.
Ivanti recommends turning off TLS 1.0 support as soon as all legacy endpoints in the environment are updated or replaced.
NTP
Add the server addresses or FQDNs of the NTP servers you want to use. File Director is configured with the addresses of three default NTP servers. If you use your own NTP servers, replace the default addresses with the addresses of your own. You can use a maximum of three NTP servers and a minimum of one.
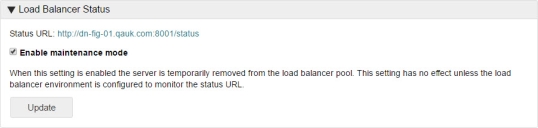
Load Balancer status
Click the Status URL link to check the health status of a server in a load balanced environment. A status page is displayed showing one of the following:
- Success - The server is functioning correctly within the load balancer pool.
- Failure - The server is either offline or is not functioning correctly within the load balancer pool.
Enable Maintenance Mode
Select Enable Maintenance Mode to temporarily take the server offline. The server is no longer available in the load balancer pool and cannot be communicated with. This allows any necessary maintenance and configuration tasks to be completed. Whilst the server is in Maintenance Mode, the status of the server shows as 'failure'.
De-select Enable Maintenance Mode to make the server available in the load balancer pool once again.
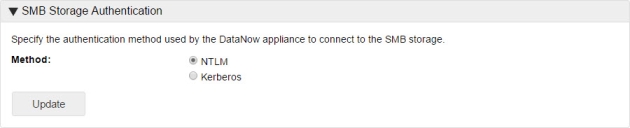
SMB storage authentication
Set the authentication method used by the File Director appliance to connect to the SMB Storage - NTLM or Kerberos.
If you select Kerberos, you must configure the Realm and Key Distribution Center (KDC) settings in the Kerberos page.
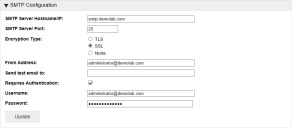
SMTP configuration
Set up SMTP to use the required account for initiating Link Based Sharing emails.
The server URL, provided in the client's request, is used to create the link included in emails to users. The File Director server URL configured for your company's appliances must be accessible externally.
- Select Configuration > Advanced.
- In the SMTP Configuration section, enter the details of the SMTP server and email
- address:
- Hostname or IP address of the SMTP server
- SMTP server port number
- Encryption type to use when sending emails
- The email address to send emails from
- Email address to receive test email
- Indicate if authentication is required and, if so, provide the username and password
- Click Update.
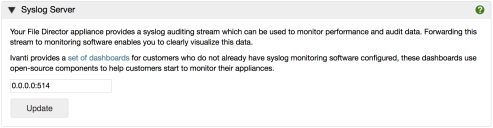
Syslog Server
Monitoring software enables you to exploit the syslog stream from your appliance and monitor the health of your File Director cluster in real time. This is strongly recommended and enables performance issues or risks to be identified early.
Ivanti provides a set of open source tools for your use including a set of three dashboards. These tools are available from Ivanti Marketplace.
File Director uses Transmission Control Protocol (TCP) to output syslog rather than User Datagram Protocol (UDP).
- Select Configuration > Advanced and scroll down to the Syslog Server section of the screen.
- Enter the IP address of the remote syslog server and click Update.
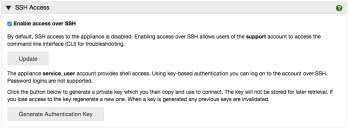
Secure Shell (SSH) Access
File Director 2019.3 introduced the SSH section to the web console. Previously it was accessible only via the VM console. If you have not yet updated to the 2019.3 release refer to the following help topic: File Director Command Line Interface.
Administrators may have requirements to access the File Director appliance over SSH connection. There are two user accounts that can be used for that purpose:
•The support account provides access to the File Director’s command line interface (CLI) which is a small set of commands used for troubleshooting and diagnostics.
•The service_user account provides non-privileged access to the underlying OS shell and enables you to, for example, perform an authenticated vulnerability scan against the appliance. Access to this account requires key-based authentication, password authentication is not allowed. You can generate a private and public key pair using the web console.
Enable / disable SSH access
SSH access is enabled or disabled via a simple checkbox. By default it is disabled.
•Select the Enable access over SSH checkbox, then click Update.
•To disable SSH access, clear the Enable access over SSH checkbox, then click Update.
Confirmation that SSH access has been updated is displayed.
Once enabled, administrators can log on using the support account and gain access to the CLI. For further information about commands available see File Director Command Line Interface.
Utilize the service_user account
To utilize the service_user account you will need to generate and deploy a public and private key pair.
1.Click Generate Authentication Key.
A public and private key pair are generated. The public key is automatically added to the trusted keys in your appliance. The private key is displayed within the SSH Access dialog.
2.Copy the private key and use it to configure the device you require to connect via SSH.
Private keys are not stored on the appliance for later retrieval. If you lose the key or wish to replace it, click Generate Authentication Key to generate a new one. Whenever a new key pair is generated, the previous keys are invalidated.